Archive for the ‘Security’ Category
Posted by //
Sean
Date //
Aug 21, 08 - 10:45 am
Categories //
Hacking
Security
Technology
Comments Off on FEMA Phones Get Hacked
 If you are going to hack a phone system, do you really want to hack the Department of Homeland Security?
If you are going to hack a phone system, do you really want to hack the Department of Homeland Security?
That’s what happened this weekend when someone made hundreds of illegal calls from a FEMA PBX to the Middle East and Asia.
It appears that it was the usual culprits of poor change control and misconfigurations left FEMA’s digital doors open.
All of this is according to an Associated Press story I read on MSNBC.com last night.
According to the AP’s Eileen Sullivan and Ted Bridis, the attacker placed more than 400 calls on the hacked FEMA phone system to places such as Afghanistan, Saudi Arabia, India and Yemen.
Here’s the kicker, from an IT security perspective, from the AP story quoting a FEMA spokesperson:
FEMA’s chief information officer is investigating who hacked into the system and where exactly the calls were placed to. At this point it appears a “hole” was left open by the contractor when the voicemail system was being upgraded, Olshanski said. Olshanski did not know who the contractor was or what hole specifically was left open, but he assured the hole has since been closed.
This illustrates an excellent, yet often overlooked, point. Despite all of the attention we spend focusing on zero-day vulnerabilities and exotic exploits and attacks – many times it’s simply poor change control procedures, lack of urgency to patch, or carelessness that gets an organization bitten.
Fortunately, in this case, it only appears to have been $12,000 in illegal calls to the Middle East and Asia, and some egg of the face of FEMA and the DHS.
Posted by //
Sean
Date //
Aug 12, 08 - 1:05 pm
Categories //
Google
Security
Technology
Comments Off on Google Says Infected Spam Is Getting Worse
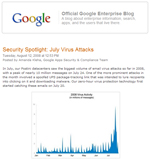 On its enterprise blog this afternoon, Google reported that it saw more infectious spam messages in July than any month so far this year.
On its enterprise blog this afternoon, Google reported that it saw more infectious spam messages in July than any month so far this year.
According to data gathered by Google’s Postini corporate e-mail security service, the volume of e-mail virus attacks peaked at almost 10 million on a single day, July 24.
That kind of volume, six to seven times what’s typical, means spam messages are getting through someone’s defenses and turning recipient’s machines into zombies, said Sundar Raghavan, a product marketing manager with the Google Apps Security & Compliance team.
“The summer of spam has caught up with us this time,” said Raghavan.
Raghavan suggests that in contrast to the message protection Google delivers from the Internet cloud, anti-spam hardware appliances that don’t update fast enough may allow malicious e-mail attacks to succeed.
Much of the spam that Google is seeing aims to exploit not browser or operating system vulnerabilities but user curiosity. Thus, explained Raghavan, spam now takes the form of spoofed CNN newsletters with link descriptions designed to bait the user, such as “Microsoft Bribes Chinese Officials.” Clicking such links in spam messages, however, generally leads to malware.
Raghavan also said that Google has seen an increase in e-mail messages with viruses concealed as encrypted .RAR attachments, despite an overall decrease in malicious attachments.
Marshal, an e-mail security company, this morning issued its security report covering the first half of 2008. In the first six months of 2008, the company says that spam volume doubled.
Marshal said that because of unpatched browsers, 45% of Internet users are at risk when they visit legitimate Web sites hosting malicious code. And there are many such sites. In May, the company identified 1.5 million Web sites infected with malware as a result of a botnet attack.
It may not come as a shock that Marshal, as a maker of e-mail security hardware, has more faith in e-mail security hardware than Google.
“We are now in the situation where spam accounts for almost 90 percent of all e-mail and increasingly contains links to infected sites,” said Bradley Anstis, VP of products, in a statement. “Companies really need to employ a combination of e-mail security gateways that have anti-spam protection using multiple techniques to block malicious content and secure Web gateway products that do not just rely on URL filtering but also scan the content that end users are downloading and uploading in real-time.”
E-mail users may also want to consider in-brain message filtering (no purchase required). Just as one might be skeptical of offers of wealth from a mysterious Nigerian benefactor, one might also refrain from clicking on links to suspect news stories along the lines of “Steve Jobs Uses Windows Vista At Home” or “Google Provides NSA With Real-Time Search Data.”
Posted by //
Sean
Date //
Aug 1, 08 - 5:23 am
Categories //
Security
Technology
Travel
Comments Off on U.S. Agents Can Seize Travelers’ Laptops
U.S. federal agents have been given new powers to seize travelers’ laptops and other electronic devices at the border and hold them for unspecified periods, the Washington Post reported this morning.
Under recently disclosed Department of Homeland Security policies, such seizures may be carried out without suspicion of wrongdoing, the newspaper said, quoting policies issued on July 16 by two DHS agencies.
Agents are empowered to share the contents of seized computers with other agencies and private entities for data decryption and other reasons.
Full story and source: Reuters
Posted by //
Sean
Date //
Jul 1, 08 - 6:33 pm
Categories //
Security
Software
Technology
Comments Off on Hey You. Yeah, You: Patch Your Web Browser
Roughly 59% of Internet users use the latest, more secure Web browsers, according to an examination of what version Web browser, down to the patch level, people are using.
That means about 576 million Web surfers leave themselves vulnerable to attack. You might just (not) be surprised by who doesn’t patch.
The study, published today, was conducted by the Swiss Federal Institute of Technology, Google, and IBM Internet Security Systems.
The researchers found that no matter how quickly browser and plug-in vendors create patches to fill security holes, it could be months before a large segment of the Internet population will apply those patches.
While I wasn’t surprised to see 83.3% of Firefox users having applied the most recent patches, the same can’t be said for Opera users, because only 56.1% of those users keep their browser up to date.
One would think that both Firefox and Opera users would be more technically savvy than the average user, thereby more prone to patch. Unlike Internet Explorer users, where less than half, at 47.6%, bother to apply the most recent software updates.
The study examined search and Web application log data from Google to ascertain what version of browsers, including patch levels, are used.
For Internet Explorer, the researchers culled data from Danish security firm Secunia’s Personal Software Inspector.
Posted by //
Sean
Date //
May 27, 08 - 9:16 am
Categories //
Security
Technology
Wireless
Comments Off on RIM To Indian Government: No Crypto Keys For You
Just last week it looked like RIM was ready to had over its Blackberry message encryption to the Indian authorities. Now, it seems as if, to quote singer/songwriter Tom Petty, RIM has had a Change of Heart.
From the chorus:
There’s been a change, Yeah there’s been a change of heart, Said there’s been a change, You push just a little too far, You make it just a little too hard, There’s been a change of heart
That’s a change from last week, when it was reported that RIM would hand over the crypto keys for its “non-business enterprise customers.”
According to a RIM statement, its encryption architecture doesn’t allow for anyone, not even RIM itself, to break open ciphered messages.
“The Blackberry security architecture for enterprise customers is purposefully designed to exclude the capability for Research in Motion or any third party to read encrypted information under any circumstances,”
Source: Indian Express Newspaper
If this is true, and I really hope it is, there is no way RIM can fulfill the Indian government’s request for the keys so they’d be able to read messages for certain investigations. Though, I’m quite confident, the government will find a way.
If they don’t, let’s see if the government ups the ante to a “don’t come around here no more” threat to RIM.
Apparently, the Indian government can’t crack 256-bit encryption to read protected e-mails on Research In Motion BlackBerrys. It appears RIM is willing to lend a hand, by handing over its (your) keys.
According to this story, which ran in The Economic Times, there’s been somewhat of a riff between the Indian Department of Telecom and RIM over BlackBerry’s inherently robust (until now) encryption.
Apparently, the Indian government can only break crypto if it’s 40 bits, or less. So they asked RIM to fork over the keys that make it possible to decrypt the messages or reduce BlackBerry crypto to 49 bits.
From the story:
According to officials close to the development, Canadian High Commissioner David Malone and RIM officials met telecom secretary Siddhartha Behura on May 7. “It was explained by RIM that it should be possible for the government to monitor e-mails to nonbusiness enterprise customers,” sources told ET. “RIM is considering giving access to individual users’ e-mail to the government. Details on this will be provided in two or three weeks,” sources said.
So it appears, for now, that corporate users don’t have as much to be concerned with.
RIM doesn’t have much more to say on the issue:
A RIM spokesperson said: “RIM operates in more than 135 countries around the world and respects the regulatory requirements of governments. RIM does not comment on confidential regulatory matters or speculation on such matters in any given country.”
I hope RIM grows more of a backbone and “respects” the privacy and security needs of its customers.
Once the keys are public, how long before the cryptography scheme is broken? How long before they’re sold to criminals? And where does this stop? Are keys going to be made available to any government that asks?